doi: 10.56294/mw2024504
ORIGINAL
Risk Assessment and Mitigation Strategies in Medical Informatics for Cybersecurity and Patient Data Protection
Evaluación de riesgos y estrategias de mitigación en informática médica para la ciberseguridad y la protección de los datos de los pacientes
Swarna
Swetha Kolaventi1 ![]() *,
Duryodhan Jena2
*,
Duryodhan Jena2 ![]() , Kothakonda Sairam3
, Kothakonda Sairam3 ![]() , Hitesh Kalra4
, Hitesh Kalra4 ![]() , Mridula Gupta5
, Mridula Gupta5 ![]() , Sumol Ratna6
, Sumol Ratna6 ![]() , Pooja Varma7
, Pooja Varma7 ![]()
1Department of uGDX, ATLAS SkillTech University, Mumbai, Maharashtra, India.
2Department of Management, Siksha ‘O’ Anusandhan (Deemed to be University), Bhubaneswar, Odisha, India.
3Centre for Multidisciplinary Research, Anurag University, Hyderabad, Telangana, India.
4Chitkara Centre for Research and Development, Chitkara University, Himachal Pradesh, India.
5Centre of Research Impact and Outcome, Chitkara University, Rajpura, Punjab, India.
6Department of General Medicine, Noida International University, Greater Noida, Uttar Pradesh, India.
7Psychology, JAIN (Deemed-to-be University), Bangalore, Karnataka, India.
Cite as: Kolaventi SS, Jena D, Sairam K, Kalra H, Gupta M, Ratna S, et al. Risk Assessment and Mitigation Strategies in Medical Informatics for Cybersecurity and Patient Data Protection. Seminars in Medical Writing and Education. 2024; 3:504. https://doi.org/10.56294/mw2024504
Submitted: 03-06-2023 Revised: 20-09-2023 Accepted: 28-01-2024 Published: 29-01-2024
Editor: PhD.
Prof. Estela Morales Peralta ![]()
Corresponding author: Swarna Swetha Kolaventi *
ABSTRACT
While combining modern technology with medical analytics has greatly improved healthcare services, it has also generated several questions over hacking and patient data protection. The risks healthcare companies confront becoming more complex as more of them use telemedicine, electronic health records (EHRs), and other digital technologies. Cyberattacks on private patient data and healthcare systems may have disastrous effects including data breaches, lost vital services, and individuals entering medical records without authorisation. Regarding hacking, this paper examines the hazards associated with medical computers with an eye on the weaknesses in the present healthcare system. It identifies the primary hazards to data integrity and patient risk including ransomware, hacking, and insider threats. Furthermore discussed in the paper are some approaches to enhance medical computer safety. Among these strategies are strong encryption, secure login systems, and continuous monitoring tools capable of locating and reacting to security concerns in real time. The article also discusses the need of strong legal frameworks requiring best practices for data security and the need of healthcare professionals learning about hacking. Furthermore underlined is the need of developing a security attitude within healthcare institutions in order to resist fresh internet risks. Finally, the study advises greater research and development to ensure patient data is safer and offers instances of improved approaches to manage risks in healthcare systems. Maintaining confidence, adhering to regulations, and the overall performance of healthcare delivery systems as healthcare providers become digital depend critically on patient data being secure and private.
Keywords: Medical Informatics; Cybersecurity; Patient Data Protection; Risk Mitigation Strategies; Healthcare System Security.
RESUMEN
Aunque la combinación de la tecnología moderna con la analítica médica ha mejorado enormemente los servicios sanitarios, también ha generado varios interrogantes sobre la piratería informática y la protección de los datos de los pacientes. Los riesgos a los que se enfrentan las empresas sanitarias son cada vez más complejos a medida que más de ellas utilizan la telemedicina, las historias clínicas electrónicas (HCE) y otras tecnologías digitales. Los ciberataques a los datos privados de los pacientes y a los sistemas sanitarios pueden tener efectos desastrosos, como la filtración de datos, la pérdida de servicios vitales y la introducción de personas en historiales médicos sin autorización. En lo que respecta a la piratería informática, este documento examina los peligros asociados a los ordenadores médicos con la vista puesta en los puntos débiles del sistema sanitario actual. Identifica los principales peligros para la integridad de los datos y el riesgo para los pacientes, como el ransomware, la piratería informática y las amenazas internas. Además, se analizan algunas estrategias para mejorar la seguridad de los ordenadores médicos. Entre estas estrategias se encuentran un cifrado fuerte, sistemas de inicio de sesión seguros y herramientas de supervisión continua capaces de localizar problemas de seguridad y reaccionar ante ellos en tiempo real. El artículo también habla de la necesidad de marcos jurídicos sólidos que exijan las mejores prácticas para la seguridad de los datos y de la necesidad de que los profesionales sanitarios aprendan sobre piratería informática. Además, subraya la necesidad de desarrollar una actitud de seguridad en las instituciones sanitarias para resistir los nuevos riesgos de Internet. Por último, el estudio aconseja una mayor investigación y desarrollo para garantizar la seguridad de los datos de los pacientes y ofrece ejemplos de enfoques mejorados para gestionar los riesgos en los sistemas sanitarios. El mantenimiento de la confianza, el cumplimiento de la normativa y el rendimiento general de los sistemas de prestación de asistencia sanitaria a medida que los proveedores de servicios sanitarios se digitalizan dependen en gran medida de que los datos de los pacientes estén seguros y sean privados.
Palabras clave: Informática Médica; Ciberseguridad; Protección de Datos de Pacientes; Estrategias de Mitigación de Riesgos; Seguridad de Sistemas Sanitarios.
INTRODUCTION
Electronic health records (EHRs), telemedicine platforms, and monitoring systems driven by artificial intelligence (AI) have become very popular in medical computing. This has led to a lot of safety problems. Strong protection standards are more important than ever as healthcare organisations depend more on linked systems to store, share, and analyse patient data. The privacy, security, and availability of sensitive medical data are very important. Any leak or exposure of this information can have very bad results, such as people getting access to private health information without permission, losing money, or even putting patients at risk. More and more often, hackers target healthcare organisations because the data they store is valuable and sensitive. This makes medical data leaks a threat to the healthcare business. More and more medical equipment, mobile health apps, and third-party providers are being added to healthcare environments, which makes data protection even harder. Each of these can cause new security holes. The dangers are always changing, and new attack methods like ransomware, scams, and insider threats are very dangerous for healthcare organisations. Also, healthcare organisations have to find a balance between the need for openness and sharing of data with the need to protect patient privacy and stop breaches. More and more private health information is being created, handled, and saved digitally. This is one of the main worries in the area of medical informatics.(1) The U.S. Department of Health and Human Services (HHS) says that the number of healthcare data breaches has hit an all-time high, with millions of patient information being accessed without permission every year. For example, there were a lot more hacks on the healthcare industry in 2020, with a record amount of ransomware strikes on hospitals and health systems. These breaches not only put patients’ privacy at risk, but they also mess up healthcare services, which could make treatment take longer and lower the level of care. Because cybersecurity is so important in healthcare, more and more people are realising that they need full risk assessment and reduction plans.
Healthcare organisations need to be cautious about hacking by looking for possible risks, putting in place means to stop them, and getting ready to respond quickly to events. As a part of those plans, advanced encryption, multi-factor login, network department, and steady tracking to identify any unusual behaviour are used. Healthcare establishments also ought to make certain that every workforce member can recognize and handle any cyber dangers.(2) That is so due to the fact one of the primary causes of the safety breaches in healthcare structures is still human error. Other than technology, legal guidelines and regulations controlling patient records safety are also instead essential for healthcare companies’ hacking rules. The general data protection regulation (GDPR) inside the EU Union and the medical health insurance Portability and duty Act (HIPAA) in the America set rigorous guidelines for the way healthcare establishments need to manage patient records and ensure that the best security measures are in region to preserve it secure from individuals who shouldn’t have get admission to it. Groups breaking statistics protection guidelines will even face extreme penalties beneath those rules. This emphasises the want of adhering to highest requirements and norms in hacking. Danger evaluation in clinical informatics is the identity and evaluation of the probably dangers to patient facts at the side of information of their implications and probability of prevalence.(3) Growing efficient risk-reducing strategies tailor-made to the hazards and susceptible factors of each healthcare organization depends on this phase of wonderful relevance. Maybe for instance, whilst studies centers might also want to keep proprietary genetic records at ease, hospitals ought to deal with maintaining scientific gadgets linked to their community secure. It makes no difference what the circumstances are; an intensive threat assessment guides healthcare establishments in figuring out where to allocate their resources and which preventive actions yield ideal effects. You have to have strong preventative plans to lessen the risks involved with hacking.
Understanding cybersecurity in medical informatics
Key Concepts of Cybersecurity in Healthcare
In order to ensure patient information is protected, guarantee systems run as they should, and safeguard private patient data, cybersecurity is very vital in healthcare. A few fundamental concepts about how to protect one from online threats are becoming evident as healthcare institutions employ more connected digital tools and systems.
· Data Protection: healthcare hacking mostly aims to keep patient data protected. Medical notes, diagnostic data, and electronic health records (EHRs) are among these things. Data has to be kept hidden so that those who shouldn’t be supposed to have access to it cannot find it. One frequent approach to keep data secure is encryption at rest as much as in action. Only authorised users of access control systems may see or alter private data.(4)
· Strong authentication techniques, such as multi-factor authentication (MFA), are required in healthcare to guarantee that those who log in are who they claim to be. Role-based access control (RBAC) guarantees that only those who really need to see certain data for their employment may access it. It limits access to sensitive information depending on user roles and obligations to do this. No one else should be able to get to the info without permission.
· Incident Response: to quickly deal with hacking or data breaches, healthcare organisations need to have clear, effective incident response plans in place. These plans show what needs to be done to stop, examine, and recover from security events. They also include steps for telling affected patients and regulatory officials what happened. Responses that are quick and clear are very important for limiting damage. Figure 1 shows cybersecurity in medical informatics, with a focus on ways to keep data safe, protect privacy, and reduce threats.
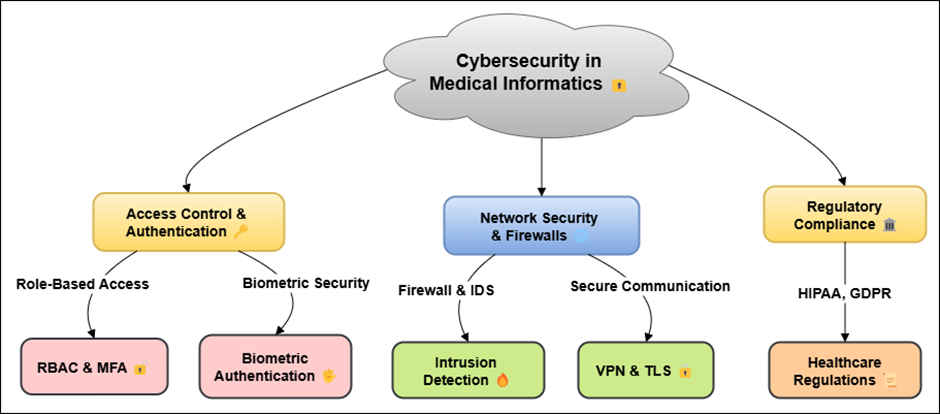
Figure 1. Illustrating Cybersecurity in Medical Informatics
· Compliance with Regulations: in the U.S. and the EU, healthcare organisations must follow the Health Insurance Portability and Accountability Act (HIPAA) and the General Data Protection Regulation (GDPR), which are rules meant to protect patient data. These rules set standards for data privacy, security, and leak reporting. They make sure that healthcare organisations protect data in the best way possible.
· Employee Training and Awareness: since mistakes made by humans are one of the main reasons for security breaches, it is important to teach healthcare workers about possible risks like phishing scams and how to handle data safely.(5) Employees are kept up to date on the latest hacking risks and the best ways to protect themselves by getting training all the time.
Types of Cyber Threats in Healthcare
Data Breaches
When someone who isn’t supposed to have access gets to sensitive patient data, like personal health information (PHI), medical records, or other private data, this is called a data breach. Data breakdowns in healthcare can be very bad. They can violate patients’ privacy, make people not trust their doctors, and even cause identity theft, insurance fraud, and medical fraud. Cybercriminals go after healthcare companies because they store a lot of valuable data and often don’t have as good of security as other industries. Data leaks can happen for many reasons, such as hacking, chance exposure, or carelessness. Hackers often get into databases with private information by using cyberattacks, like taking advantage of holes in a healthcare system’s network infrastructure, or by getting login information.(6) Internal breaches can also happen when workers share private information without meaning to or don’t follow the rules for keeping data safe. Loss or theft of computers, USB drives, or other devices that have patient information on them without the right security or access limits can also lead to data breaches. Data breaches have effects that go beyond the direct costs of money like fines and court fees. They can hurt a company’s image, make patients less likely to believe them, and cause trouble with the law and regulations for a long time. So, to stop data breaches, you need a complete plan that includes strong cybersecurity measures like firewalls, intrusion detection systems, and strong encryption.(7) You also need to train your employees regularly on data safety and how to handle patient information safely. Healthcare organisations also need to have incident reaction plans in place so that they can quickly find, limit, and deal with breaches so that they have as little of an effect as possible.
Ransomware Attacks
Ransomware attacks are becoming more common in the healthcare field. Cybercriminals use harmful software to lock a healthcare organization’s files or systems, making them impossible to access. Attackers usually ask for a fee to unlock the files. If you don’t pay, you could lose important data forever or have healthcare services stop working as usual. Ransomware can make hospitals, clinics, and other healthcare workers unable to do their jobs by blocking access to patient records, scheduling systems, testing tools, and other important functions. This can put patients’ health at risk. Phishing emails or harmful files are often used in these attacks to get employees to download the ransomware. Malware can quickly spread through a network after it is installed.(8) It locks down files and asks for payment, usually in cryptocurrency, to open them. Healthcare organisations are more likely to be hit by ransomware because their patient data is important and taking systems offline could affect how well patients are cared for. In addition to the problems they cause right away, ransomware attacks can have very bad effects in the future as well. Along with the cash payments, companies may have to pay large fines for not keeping patient data safe, face lawsuits, and pay to rebuild their IT systems. To keep themselves safe from ransomware, healthcare organisations need to spend money on things like regular data backups, network segmentation, and device security.
Phishing and Social Engineering
Phishing and social engineering are common types of cyber risks that involve tricking people into giving up private information or doing things that are bad for security. Attackers often go after healthcare workers and staff, taking advantage of their trust or lack of knowledge to get to private patient information, login information, or internal systems. Phishing usually involves fake emails or messages that look like they came from a real person, like a co-worker, a manager, or a trusted third-party seller.(9) The emails or messages invite the recipient to open compromised files or click on dangerous links. Though they are more complicated and include a greater spectrum of techniques to exploit people’s vulnerabilities, social engineering schemes resemble hacking in some respects. Pretexting in which an assailant creates a narrative or scenario to get private information or baiting, in which an assailant presents something enticing to encourage the victim to act like acquiring dangerous software could both be included here. Social engineering assaults in the context of healthcare might include utilising patient information to commit theft or posing as a healthcare practitioner gaining access to patient records without authorisation. Attacks via phishing and social engineering may have disastrous effects including data breaches, financial fraud, medical information being accessed by someone unfit for access, and system security being compromised.(10) These acts also make it harder for people and healthcare workers to trust each other.
Regulatory Frameworks for Patient Data Protection
HIPAA (Health Insurance Portability and Accountability Act)
The United States’ Health Insurance Portability and Accountability Act (HIPAA), which was passed in 1996, is a key set of rules meant to protect patient privacy and keep healthcare data safe. Health care workers, health companies, healthcare clearinghouses, and their business partners who deal with protected health information (PHI) must follow HIPAA. National guidelines for protecting health information are set by the act. This makes sure that patients’ data is kept private, safe, and only readable by people who are allowed to. The main goal of HIPAA is to keep patients’ personal and health-related information from getting into the wrong hands or being shared without permission. It tells healthcare organisations exactly how to handle, store, and send patient data. It stresses how important encryption, safe access controls, and identification procedures are. Under HIPAA, organisations that are protected must put in place physical, administrative, and digital protections to keep patient data private, accurate, and accessible. The act also says that healthcare organisations must teach their workers how to properly handle data and do regular risk reviews to find any weak spots in their systems.(11) The Privacy Rule is an important part of HIPAA because it says how health information should be shared and kept safe. It requires healthcare workers to get permission from patients before sharing their medical records for reasons other than treatment. The Security Rule goes along with the Privacy Rule. It sets guidelines for how health information should be protected electronically. For example, it requires encryption, secure contact routes, and multi-factor identification. HIPAA also has rules about breach reporting. If there is a data hack involving PHI, organisations must tell the people who were affected and the government.(12) If healthcare organisations break HIPAA rules, they could face serious consequences, such as fines and damage to their image.
GDPR (General Data Protection Regulation)
The European Union passed the General Data Protection Regulation (GDPR) in 2018. It is a general rule meant to protect people’s privacy and personal data in the EU and the European Economic Area (EEA). General Data Protection Regulation (GDPR) mostly affects businesses in the European Union (EU), but it also affects businesses outside of the EU that handle personal data of EU citizens. GDPR is thought to be one of the strictest data security rules in the world. It increases individuals’ personal data control, including private medical records. Health data is referred to as “special category data,” under GDPR, and because it is so sensitive requires additional protection. Healthcare companies holding personal health data have to strictly handle and store data.(13) These guidelines guarantee that data is only collected for legal purposes and isn’t stored longer than absolutely necessary. To protect personal health data from anyone who shouldn’t have access to it or from being stolen, GDPR also mandates robust encryption, anonymization, and access control be used by businesses. Based on the concept of “data subject rights,” GDPR holds that individuals have the right to inspect, alter, delete, or restrict how their personal data is handled. This covers their right to alter their opinion about the processing of their data at any moment, therefore empowering them over their medical records.(14)
National and International Guidelines
Protection of affected person information and making sure that healthcare statistics is protected in all spheres rely upon each national and worldwide policies being carried out. By means of defining guidelines for the secure treatment, maintenance, and switch of patient information, those guidelines offer corporations the standards they need to shield personal health information. Operating with rules like HIPAA and GDPR, national and global requirements assist to cope with sparkling dangers and troubles arising as healthcare era broaden. Each nation has advanced policies for healthcare facts protection and hacking at the country wide degree; these regulations are typically changed to fulfil the legal guidelines, subculture, and healthcare device of the state. Other than HIPAA, the U.S. Centres for Medicare and Medicaid services presents guidelines for healthcare professionals on facts safety enhancement and protection of electronic health statistics. Furthermore, the U.S. country wide Institute of standards and generation expand cybersecurity structures utilized in several spheres, along with healthcare.(15) These models encompass tips for controlling dangers, preserving gadget integrity, and managing cyber incidents. legal guidelines like the non-public health records protection and electronic Transactions Act in Canada and the Australian privacy ideas in Australia provide hints on a way to securely manage health records even as nonetheless safeguarding patients’ privateness in places like Canada and Australia. These countrywide guidelines purpose to set up safety protocols, methods of handling authorisation, and approach of reporting breaches thereby reducing the risks of facts leaks and unlawful access. Approaches, problems, future trends, and rewards of cybersecurity in medical information systems are summed up in table 1.
|
Table 1. Summary of Cybersecurity in Medical Informatics |
|||
|
Approach |
Challenges |
Future Trend |
Benefits |
|
Risk Assessment Framework |
Limited Budget for Security |
Automated Risk Assessment |
Improved Risk Detection and Mitigation |
|
Data Encryption |
High Implementation Cost |
Advanced Encryption Algorithms |
Enhanced Data Protection |
|
Access Control |
Complexity in Managing Access |
Zero Trust Architecture |
Increased Control Over Sensitive Data |
|
Employee Training Programs |
Resistance to Change |
Gamified Training |
Reduced Human Error |
|
Incident Response Plan(16) |
Unpredictable Attack Vectors |
AI-Driven Response Systems |
Faster Response to Security Incidents |
|
Multi-Factor Authentication |
High Resource Demand for MFA |
Biometric Authentication |
Enhanced Security Posture |
|
Cloud Security Solutions |
Integration with Existing Infrastructure |
AI-Powered Cloud Security |
Secure and Scalable Cloud Environment |
|
Blockchain Technology |
Regulatory Compliance Issues |
Smart Contracts on Blockchain |
Tamper-Proof Records |
|
AI-Based Threat Detection |
Evolving Cyber Threats |
Enhanced AI in Threat Detection |
Proactive Threat Detection |
|
Regular Audits |
Staff Training & Awareness |
Real-Time Audit Systems |
Compliance with Regulations |
|
Role-Based Access Control |
Balancing Accessibility with Security |
Behavioral Analytics in Access Control |
Efficient and Secure User Access |
|
Data Masking(17) |
Ensuring Data Integrity |
Dynamic Data Masking |
Minimized Data Exposure |
|
Compliance Monitoring |
Keeping Up with Legal Changes |
Real-Time Compliance Monitoring |
Ensure Legal Compliance |
|
Continuous System Monitoring |
Cybersecurity Resource Shortage |
Autonomous Security Systems |
Constant Threat Monitoring |
Risk assessment in medical informatics
Identifying Risks in Healthcare Systems
Finding risks in healthcare systems is an important first step in managing risks in general. There are a lot of risks in healthcare settings because they use complicated tools, have a lot of pros, and handle private patient information. These risks include online attacks, operating fails, data breaches, and mistakes made by people. All of these things can have a big effect on patient care, safety, and privacy. The main sources of risk in medical informatics are digitalising patient information, using cloud-based systems to store and process health data, and gadgets that are linked to each other. These things make healthcare systems vulnerable, and they need to be carefully checked for and controlled to make sure they work safely and well. There are four main types of risks in healthcare systems: technology risks, human factors risks, organisational risks, and legal risks. Threats like malware, ransomware, and data breaches are examples of technical risks. System breakdowns and software bugs are also examples. Healthcare workers’ mistakes, like bad data handling, misunderstandings, or not following security rules, are often caused by human factors.(18) Regulatory risks come from not following data protection and privacy laws and rules like GDPR and HIPAA. Organisational risks come from not having enough security policies, training, and event response plans. To find these risks, you need to know a lot about how healthcare works, how technology is used, and who might be trying to do harm to healthcare institutions. Regular evaluations and checks, along with feedback from a range of partners, are necessary to successfully identify and classify risks.
Risk Analysis Methods
Qualitative Assessment
Usually, the rating for risks is based on their likelihood of stopping activities, endangering patients, or violating the laws. Their severity degree high, medium, or low then determines how they are examined. By examining historical assaults, system vulnerabilities, and current security policies, an expert group may determine, for example, the likelihood that ransomware would strike. When someone needs a rapid, all-encompassing view of the hazards or when they cannot access numerical data, they commonly employ this approach. Qualitative evaluations have one flaw in that they are subjective, which makes it difficult to regularly evaluate hazards. However, qualitative assessments provide valuable information on prospective hazards and enable the development of a comprehensive risk management strategy when used in line with quantitative techniques.
Quantitative Assessment
Unlike qualitative analysis, quantitative risk assessment determines the degree of risk by use of numerical values and statistical models. Usually this approach is used to estimate the probability and influence of hazards in terms of certain values. For instance, determining the probability of a hack and the related prospective financial or pragmatic consequences. In medical computing, quantitative studies can rely on prior data, comparable measures from healthcare institutions, and models to determine the degree of risk and the likely results. For instance, healthcare providers might use statistical models to guess how often data breaches or ransomware attacks happen and figure out how much they cost by looking at averages in the industry. The best thing about quantitative surveys is that they give organisations clear, data-based results that help them decide which risks are most important and where to put their resources most efficiently. But this method might not work if there isn’t enough clear data, especially in places where risk is new. It can also be hard to put a number on risks in healthcare settings that are very changeable, where things like the amount of patient data or the number of gadgets that are tied to each other change all the time.
Risk Prioritization in Healthcare
Risk prioritisation is the process of figuring out which risks are the most dangerous to a healthcare organisation and need to be dealt with first. In medical computing, putting risks in order of importance is important to make sure that resources are used wisely to fix the most serious problems. Usually, both qualitative and quantitative studies are used to guide this process. These help organisations figure out how likely different risks are to happen and how bad they could be if they do. Once healthcare organisations know what risks there are, they have to put them in order of importance based on things like how bad they are, how likely they are to happen, how they might affect regulations, and how they might affect patient care. For example, a risk like a possible ransomware attack might be given a lot of attention because it could stop the hospital from running, keep important patient data from being accessed, and require expensive repair work. In the same way, the risks of not following data security rules (like GDPR or HIPAA violations) could be rated high because of the fines and legal problems that come with not following the rules. Risk grids or heat maps are often used by healthcare organisations to show and rank risks based on how likely they are to happen and how bad they would be if they did. This helps people who have to make decisions focus on the most important problems and take the right steps to lower their risk exposure. Healthcare is a fast-paced and high-stakes field. Good risk prioritisation makes sure that healthcare workers have the tools they need to keep patient data safe, follow the rules, and protect the dignity of healthcare systems.
Mitigation strategies for cybersecurity risks
Technical Solutions
Encryption and Data Masking
Information hiding and encryption are two key technological tools used to defend personal patient facts and prevent unauthorised users from getting into healthcare networks. Encryption alters facts that can be examined into an inaccessible code with the aid of use of secure techniques. Which means that without the correct interpreting key, information can’t be interpreted although it’s far stolen or visible with the aid of adverse people. Healthcare can’t operate without electronic health data (EHRs), patient clinical facts, and financial statistics secured. It need to be utilised each in movement—sent throughout networks—and at rest—this is, whilst saved on gadgets or computer systems—to offer complete safety. While private records is sent between coverage, out of doors businesses, and healthcare companies, cease-to- quit encryption also guarantees its safety. Information concealing is every other method wherein personal facts consisting of social protection numbers or scientific data is hidden the use of bogus or anonymised information. Although personal statistics is masked to safeguard confidentiality, the facts may additionally nevertheless be utilised for obligations like software program trying out and evaluation. This method plays especially well in test environments or when distributing healthcare data to different corporations when complete information access isn’t required. Data filtering reduces the possibility of unintentional information get entry to or leaks occurring at some stage in information control. maintaining patient agree with, following HIPAA and GDPR, and making sure that regulations are accompanied depend upon both encryption and facts concealing, which can be pretty critical for protecting healthcare information.
Access Control and Authentication
Crucial technological gear for maintaining patient facts secure and preventing the ones not intended to be there from getting into healthcare systems are get entry to control and identification. Who may see what data or use certain equipment and what they may do once they do so is determined by way of get entry to control. In healthcare, get entry to control ensures that best accredited employees inclusive of managers, nurses, and docs might also see or regulate exclusive patient records. commonly according to the least privilege (POLP) concept, which holds that people need to simplest possess the understanding required for their employment, people this technique reduces the possibility of facts breaches or unauthorised get entry to via proscribing who may additionally see personal facts. Together with get entry to manipulate, authentication guarantees that handiest real users might also access healthcare systems. Sturdy security systems such as multi-element authentication demand users to affirm their identity in many ways earlier than they may get entry to private facts. MFA might combine personal records like a fingerprint or facial recognition, what a person is aware of like a password what they have got like a smart card or phone and what they’re. By means of presenting a couple of strains of defence, MFA substantially enhances protection and decreases the likelihood that someone will input without authorisation using susceptible or stolen credentials.
Organizational Strategies
Employee Training and Awareness Programs
Vital strategies for healthcare structures lowering their hacking threats consist of education and education campaigns for team of workers participants. Coaching healthcare experts a way to preserve statistics, perceive potential risks, and observe protection policies can help to maintain the environment safe as human blunders is a primary issue of protection breaches. These guides of preparation must cowl an extensive spectrum of cybersecurity topics, consisting of a way to recognize phoney emails, why robust, precise passwords are crucial, and how to correctly manage personal affected person information. Regarding data protection, personnel must additionally be taught their precise duties and duties in addition to the suggestions and procedures for documenting safety occurrences or uncommon pastime. Healthcare team of workers contributors also need to be instructed in adhering to facts safety requirements which include HIPAA and GDPR. Knowing those suggestions ensures that personnel members apprehend what they have to accomplish and what is going to appear need to they fail. Workers have to be modern-day on new cybersecurity risks, new generation, and legislative modifications because the digital world and cyber perils expand hastily. By using making employees greater proactive and vigilant, common safety exams and hacker simulations permit them to understand how critical it is to hold private affected person information protected. Healthcare agencies may also reduce the risks on account of insider threats, human error, and negligent behavior by way of raising everyone’s information of cybersecurity.
Incident Response Plans
Good Incident response Plans (IRP) is crucial for healthcare establishments to fast and successfully deal with hacking occurrences, consequently decreasing the damage as a result of assaults or breaches. An IRP lays down precisely what need to be achieved should a hack, facts leak, or other safety issue get up. This guarantees that medical experts may also respond speedy and with efficiency. in conjunction with the movements to minimise, check out, and bounce back from an occurrence, the approach need to simply outline each crew member’s obligations and duties. While legal and compliance teams manage informing impacted patients and regulatory government approximately the issue, IT employees may be in price of separating the impacted structures. An IRP depends tons on effective conversation both inside and out of doors of the enterprise because it ensures that everybody engaged is privy to what transpired and that the perfect movements are finished. this could also consist of informing sufferers whose records has been compromised and ensuring that the suitable channels of movement are observed to address issues and keep confidence for healthcare institutions. furthermore covered within the IRP ought to be strategies for accomplishing an evaluation after an incident to check the source of the breach, examine the effectiveness of the reaction, and guide destiny preparations.
Challenges in implementing risk mitigation strategies
Budget Constraints and Resource Allocation
One of the main challenges healthcare institutions has when trying to use risk-reducing strategies is financial ones. Reducing resources might make using cutting edge hacking tools, training staff members, and following data security regulations more difficult. Particularly in medical informatics, cybersecurity threats are becoming more complex and widespread, so it is crucial to make appropriate use of resources to reduce risks. However, many times, healthcare companies prioritise operating the company and patient care over cybersecurity expenses. Security systems and technologies so get inadequate funding. Many healthcare systems, particularly smaller or rural ones, have little resources, so there is not much for defence programs. Establishing complete security mechanisms including firewalls, breach detection systems, safe communication channels, and encryption may be somewhat expensive. Likewise, the financial weight is further increased by the expenses of regular inspections to ensure staff is following industry standards and continuous training programs for them. This means that healthcare companies may use disorganised or antiquated security systems that expose them to hackers, data leaks, or noncompliance problems.
Balancing Data Accessibility with Security
Every other tough venture in enforcing chance-lowering methods in healthcare is striking the suitable balance between information security and usability. To offer fast and green remedy, healthcare institutions need to ensure that approved employees may additionally easily get right of entry to affected person information. Making this information public at the same time as simultaneously making sure it is comfy against robbery, unlawful access, and different negative applications is hard, but. On the one hand, making picks requires rapid and easy get right of entry to affected person information and other confidential facts for healthcare experts. Waiting too lengthy to get important statistics in an emergency might compromise affected person remedy greatly. When users want to enter a gadget, it may be weak if the proper security mechanisms inclusive of encryption, get entry to regulations, and identification verification are absent. As an example, excessively rigorous front rules would possibly sluggish down medical professionals’ paintings, infuriating them and maybe suspending affected person treatment. Complicated safety regulations may make it difficult for healthcare experts in particular in critical or emergency care environments to get admission to statistics as wished. Healthcare institutions must create safety strategies allowing users too hastily and securely get right of entry to records in the event that they want to deal with this venture. This covers role-primarily based get right of entry to manage rules ensuring employees may additionally best get right of entry to the statistics they require relying on their roles as well as personal communication channels and multi-factor identity to higher protect data.
RESULTS AND DISCUSSION
In medical computing, research on risk assessment and strategies for reduction reveals some really significant findings. First of all, healthcare companies deal with major cybersecurity issues like hacker scams, ransomware attacks, and data breaches. The way healthcare is managed and patient data’s safety may be greatly impacted by these hazards. Strong encryption, multi-factor identification, and secure communication channels have all been shown to help to reduce the likelihood that private information may be accessed by someone not intended for that. However, limited resources often make it hard to adopt full protection.
|
Table 2. Cybersecurity Risks and Mitigation Strategies |
||||
|
Cybersecurity Risk |
Likelihood (%) |
Impact (%) |
Mitigation Effectiveness (%) |
Priority Score (Likelihood * Impact) |
|
Data Breaches |
97 |
95 |
81,4 |
25 |
|
Ransomware Attacks |
82 |
92 |
95,9 |
20 |
|
Phishing |
80 |
88,4 |
80,5 |
16 |
|
Insider Threats |
67 |
80 |
66,6 |
12 |
|
System Vulnerabilities |
60 |
63,5 |
83 |
9 |
In medical informatics, table 2 gives an in-depth look at different hacking risks and the ways that they can be reduced. With a ranking number of 25, Data Breaches have the best chance (97 %) and effect (95 %). This shows how important it is to have strong security measures, since data breaches are a major threat to patient privacy and the dignity of organisations. Figure 2 shows a comparison of the possibility and effect of hacking risks, showing where healthcare systems are weak and what could happen.
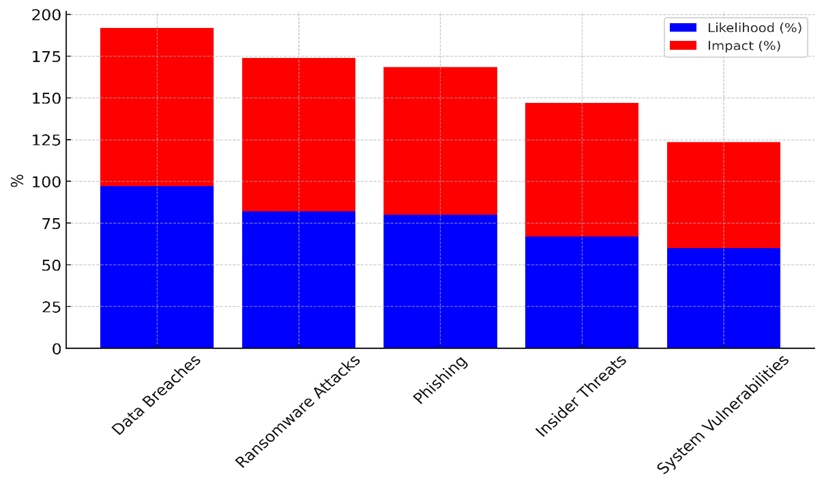
Figure 2. Comparison of Cybersecurity Risk Likelihood and Impact
Ransomware attacks are very likely to happen (82 % of the time) and have a high impact (92 % of the time). However, they are also very easy to stop (95,9 % of the time) with backups and encryption, among other things. Trends in hacking risks are shown in Figure 3. The graph focuses on chance, effect, attempts to reduce risks, and priority levels.
Ransomware threats are very bad, but they can be stopped by taking proactive security steps, giving them an importance score of 20. With an 80 % chance of happening and an 88,4 % impact, phishing attacks are still a regular threat, and prevention is only 80,5 % successful. To lower risks, healthcare workers need to be constantly educated about phishing. Insider threats are a more controllable but still serious threat. Figure 4 is a stacked diagram of hacking risk factors that shows how they affect and are important in comparison to each other.
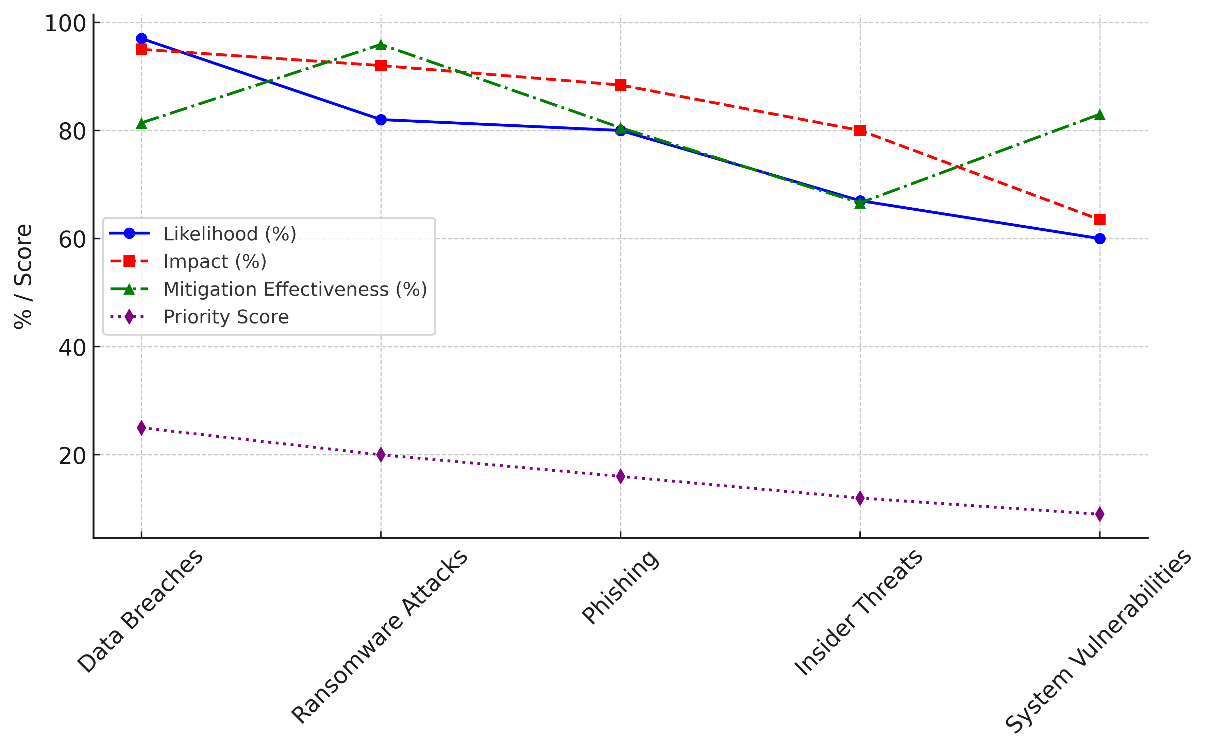
Figure 3. Trends in Cybersecurity Risks: Likelihood, Impact, Mitigation, and Priority
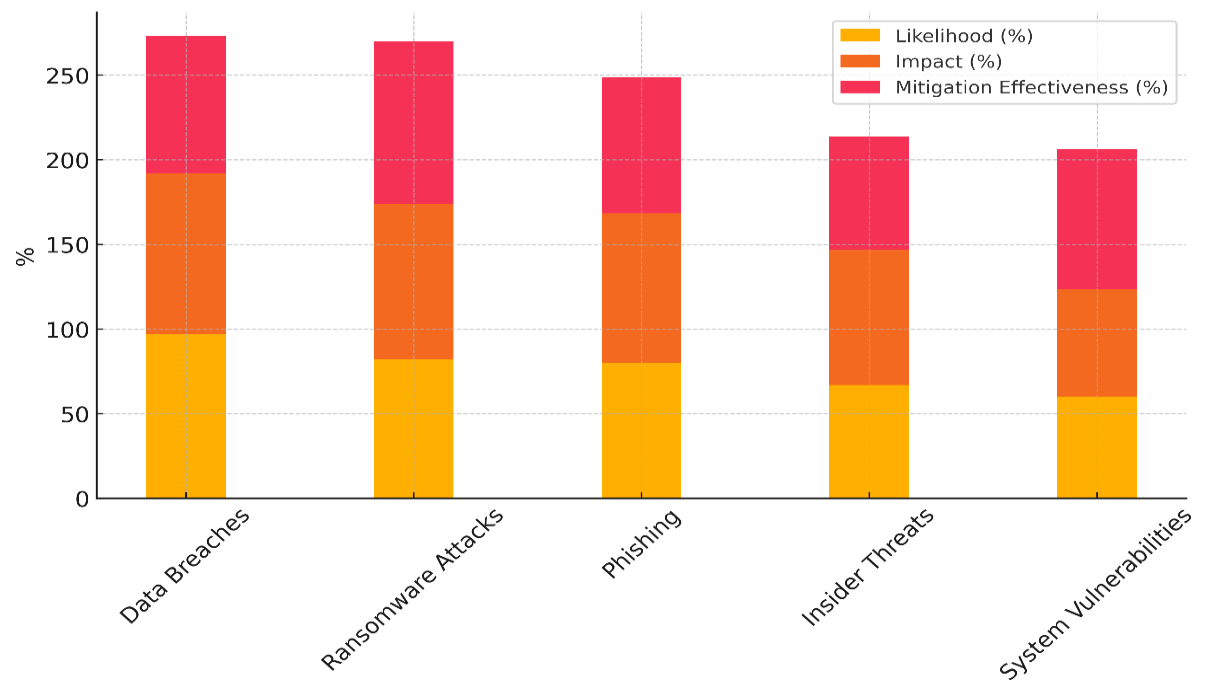
Figure 4. Stacked Representation of Cybersecurity Risk Factors
They happen 67 % of the time and have an 80 % success rate. Insider risks are mostly dealt with by keeping an eye on employees and controlling who can see what. This is why the priority score is 12. Lastly, System Vulnerabilities have a lower chance of happening (60 % chance) and a higher impact (63,5 %), but they are still important, and effective ways to fix them guarantee a priority number of 9.
|
Table 3. Risk Mitigation Techniques Evaluation (%) |
||||
|
Mitigation Strategy |
Implementation Cost (%) |
Effectiveness (%) |
Resource Requirement (%) |
Implementation Time (%) |
|
Encryption |
63 |
100 |
60 |
40 |
|
Multi-Factor Authentication |
80 |
94 |
85 |
63 |
|
Employee Training |
45 |
80,6 |
69 |
88 |
|
Incident Response Plan |
82 |
97 |
81 |
60 |
Table 3 compares different ways to reduce risk by looking at how much they cost, how well they work, what resources they need, and how long it takes to apply them. The results show that encryption is a very good plan that only needs a few resources and doesn’t cost much to set up (63 %). Because it only takes 40 % of the time to set up, it’s a useful way to protect private data that will be used by all healthcare systems. Multi-Factor Authentication (MFA) costs a lot to set up (80 %), but it works very well (94 % of the time) to make things safer figure 5 shows a comparison of different cybersecurity tactics for healthcare systems based on their prices, resources, efficiency, and time to adopt.
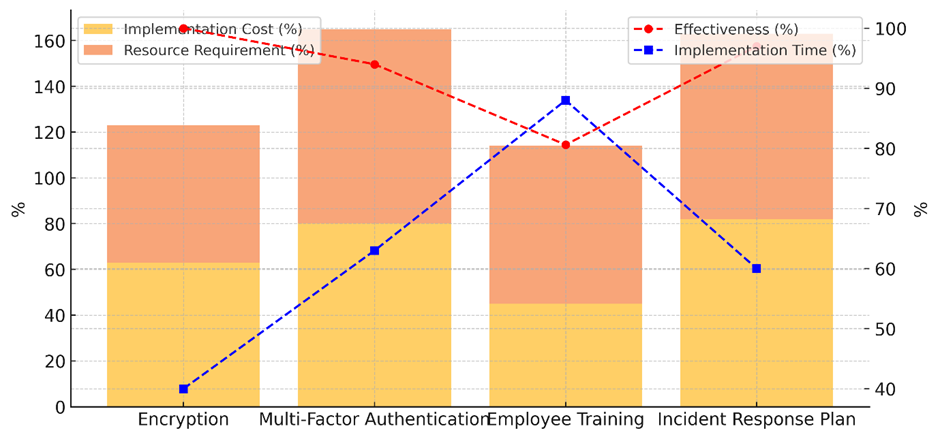
Figure 5. Comparison of Cybersecurity Mitigation Strategy Costs, Resources, Effectiveness, and Implementation Time
It needs a lot of resources (85 %) and will take a long time to implement (63 %), which shows that it needs to be carefully planned and embraced by users. Even though it costs more and requires more resources, MFA is a strong way to keep people from getting in without permission, which makes it a good approach for healthcare organisations. Figure 6 shows the total amount of money that it takes to adopt protection measures, showing how they affect money over time.
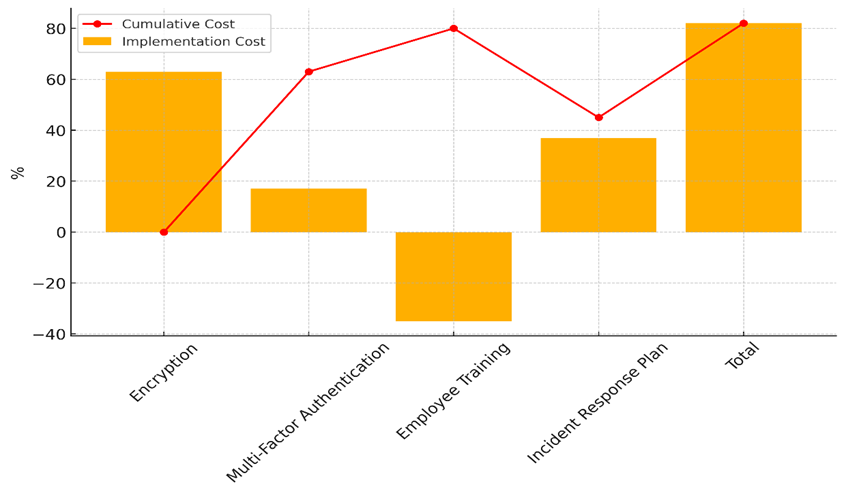
Figure 6. Cumulative Implementation Costs of Cybersecurity Mitigation Strategies
Training employees is the most cost-effective approach (45,6 %) and also one of the least successful. It doesn’t need many resources (69 %) but takes a long time to put into action (88 %), because ongoing education and knowledge are important to stop mistakes and hacking attacks. Lastly, the Incident Response Plan works very well (97 % of the time) but uses a lot of resources (81 % of the time). It also takes a lot of time to set up (60 % of the time), which makes it an important strategy for acting quickly to security breaches. Even though it costs money, the benefits of quick reaction and recovery make it worth it for healthcare protection.
CONCLUSION
In medical computing, keeping patient data safe and private is a difficult but important job. There are more risks like data breaches, hacking, and internal threats in healthcare systems because they are becoming more digital very quickly. Plans must include technological solutions, organisational methods, and policy actions if they are to properly lower risks. By preventing online threats before they arise and allowing one to react when they do arise, technologies such encryption, blockchain, and artificial intelligence help safeguard healthcare data. But implementing these ideas mostly depends on how resources are distributed, how frequently staff members get training, and how tightly the system is always under observation. Implementing these ideas comes with a major challenge as many times healthcare institutions lack the necessary funds. Smaller institutions may find it difficult to purchase the most recent security measures, hence healthcare facilities must carefully choose which investments to undertake depending on the associated risks. Following the guidelines and safeguarding private patient data assist ensure that resources are allocated where they are most needed. Finding the proper balance between data usefulness and security is also difficult constantly. Healthcare professionals must, for instance, rapidly access data to provide timely treatment, but they also have to ensure that rigorous security policies do not impede process flow. Adding role-based access rules and making it easier for IT security teams and healthcare staff to talk to each other can help with this problem. Another problem is getting healthcare organisations to accept change. This can be lessened by offering thorough training, showing how important safety is, and making sure that new systems meet the needs of healthcare workers.
REFERENCES
1. Al-Araji, Z.J.; Ahmad, S.S.S.; Abdullah, R. Attack Prediction to Enhance Attack Path Discovery Using Improved Attack Graph. Karbala Int. J. Mod. Sci. 2022, 8, 313–329.
2. Kanakogi, K.; Washizaki, H.; Fukazawa, Y.; Ogata, S.; Okubo, T.; Kato, T.; Kanuka, H.; Hazeyama, A.; Yoshioka, N. Tracing cve vulnerability information to capec attack patterns using natural language processing techniques. Information 2021, 12, 298.
3. Snmez, F.Z.; Hankin, C.; Malacaria, P. Attack dynamics: An automatic attack graph generation framework based on system topology, CAPEC, CWE, and CVE databases. Comput. Secur. 2022, 123, 102938.
4. Kure, H.; Islam, S.; Ghazanfar, M.; Raza, A.; Pasha, M. Asset criticality and risk prediction for an effective cybersecurity risk management of cyber-physical system. Neural Comput. Appl. 2021, 34, 493–514.
5. Melaku, H.M. Context-Based and Adaptive Cybersecurity Risk Management Framework. Risks 2023, 11, 101.
6. Zeng, Z.; Yang, Z.; Huang, D.; Chung, C.-J. LICALITY—Likelihood and Criticality: Vulnerability Risk Prioritization Through Logical Reasoning and Deep Learning. IEEE Trans. Netw. Serv. Manag. 2022, 19, 1746–1760.
7. Kanakogi, K.; Washizaki, H.; Fukazawa, Y.; Ogata, S.; Okubo, T.; Kato, T.; Kanuka, H.; Hazeyama, A.; Yoshioka, N. Comparative Evaluation of NLP-Based Approaches for Linking CAPEC Attack Patterns from CVE Vulnerability Information. Appl. Sci. 2022, 12, 3400.
8. Mizrak, F. Integrating Cybersecurity Risk Management into Strategic Management: A Comprehensive Literature Review. Res. J. Bus. Manag. 2023, 10, 98–108.
9. Kotsias, J.; Ahmad, A.; Scheepers, R. Adopting and integrating cyber-threat intelligence in a commercial organisation. Eur. J. Inf. Syst. 2023, 32, 35–51.
10. Ferreira, D.J.; Mateus-Coelho, N.; Mamede, H.S. Methodology for Predictive Cyber Security Risk Assessment (PCSRA). Procedia Comput. Sci. 2023, 219, 1555–1563.
11. Cheimonidis, P.; Rantos, K. Dynamic Risk Assessment in Cybersecurity: A Systematic Literature Review. Future Internet 2023, 15, 324.
12. Tanmaya Kumar Swain. (2015). Research & Development : Higher Education in India. International Journal on Research and Development - A Management Review, 4(2), 53 - 58.
13. El Amin, H.; Oueidat, L.; Chamoun, M.; Samhat, A.E.; Feghali, A. Blockchain-based multi-organizational cyber risk management framework for collaborative environments. Int. J. Inf. Secur. 2023, 23, 1231–1249.
14. Djenna, A.; Harous, S.; Saidouni, D.E. Internet of Things Meet Internet of Threats: New Concern Cyber Security Issues of Critical Cyber Infrastructure. Appl. Sci. 2021, 11, 4580.
15. Echeverría, A.; Cevallos, C.; Ortiz-Garces, I.; Andrade, R.O. Cybersecurity Model Based on Hardening for Secure Internet of Things Implementation. Appl. Sci. 2021, 11, 3260.
16. Almomani, O.; Almaiah, M.A.; Alsaaidah, A.; Smadi, S.; Mohammad, A.H.; Althunibat, A. Machine learning classifiers for network intrusion detection system: Comparative study. In Proceedings of the 2021 International Conference on Information Technology (ICIT), Amman, Jordan, 14–15 July 2021; pp. 440–445.
17. Lin, Z.; Lin, M.; Champagne, B.; Zhu, W.-P.; Al-Dhahir, N. Secrecy-Energy Efficient Hybrid Beamforming for Satellite-Terrestrial Integrated Networks. IEEE Trans. Commun. 2021, 69, 6345–6360.
18. Lin, Z.; An, K.; Niu, H.; Hu, Y.; Chatzinotas, S.; Zheng, G.; Wang, J. SLNR-based Secure Energy Efficient Beamforming in Multibeam Satellite Systems. IEEE Trans. Aerosp. Electron. Syst. 2022, 59, 2085–2088.
FINANCING
None.
CONFLICT OF INTEREST
The authors declare that the research was conducted without any commercial or financial relationships that could be construed as a potential conflict of interest.
AUTHORSHIP CONTRIBUTION
Conceptualization: Swarna Swetha Kolaventi, Duryodhan Jena, Kothakonda Sairam, Hitesh Kalra, Mridula Gupta, Sumol Ratna, Pooja Varma.
Data curation: Swarna Swetha Kolaventi, Duryodhan Jena, Kothakonda Sairam, Hitesh Kalra, Mridula Gupta, Sumol Ratna, Pooja Varma.
Formal analysis: Swarna Swetha Kolaventi, Duryodhan Jena, Kothakonda Sairam, Hitesh Kalra, Mridula Gupta, Sumol Ratna, Pooja Varma.
Research: Swarna Swetha Kolaventi, Duryodhan Jena, Kothakonda Sairam, Hitesh Kalra, Mridula Gupta, Sumol Ratna, Pooja Varma.
Methodology: Swarna Swetha Kolaventi, Duryodhan Jena, Kothakonda Sairam, Hitesh Kalra, Mridula Gupta, Sumol Ratna, Pooja Varma.
Project management: Swarna Swetha Kolaventi, Duryodhan Jena, Kothakonda Sairam, Hitesh Kalra, Mridula Gupta, Sumol Ratna, Pooja Varma.
Resources: Swarna Swetha Kolaventi, Duryodhan Jena, Kothakonda Sairam, Hitesh Kalra, Mridula Gupta, Sumol Ratna, Pooja Varma.
Software: Swarna Swetha Kolaventi, Duryodhan Jena, Kothakonda Sairam, Hitesh Kalra, Mridula Gupta, Sumol Ratna, Pooja Varma.
Supervision: Swarna Swetha Kolaventi, Duryodhan Jena, Kothakonda Sairam, Hitesh Kalra, Mridula Gupta, Sumol Ratna, Pooja Varma.
Validation: Swarna Swetha Kolaventi, Duryodhan Jena, Kothakonda Sairam, Hitesh Kalra, Mridula Gupta, Sumol Ratna, Pooja Varma.
Display: Swarna Swetha Kolaventi, Duryodhan Jena, Kothakonda Sairam, Hitesh Kalra, Mridula Gupta, Sumol Ratna, Pooja Varma.
Drafting - original draft: Swarna Swetha Kolaventi, Duryodhan Jena, Kothakonda Sairam, Hitesh Kalra, Mridula Gupta, Sumol Ratna, Pooja Varma.
Writing: Swarna Swetha Kolaventi, Duryodhan Jena, Kothakonda Sairam, Hitesh Kalra, Mridula Gupta, Sumol Ratna, Pooja Varma.